UPDATE: Since this article was published, a new server package has been built that’s even better for use with Delta Chat. The new server is called Chatmail and its open-source repository is here. Also see: Using Delta Chat with Chatmail servers for decentralized, open, secure, private messaging. The below instructions are still valid if you want to make a server that supports both encrypted Delta Chat communications as well as regular federated email.
If you’ve been watching what’s been happening to Twitter since it was bought out by Elon Musk, you might have recently realized the advantages of using more sustainable, federated, decentralized, and open technologies (Such as Mastodon and the Fediverse). Or maybe you realized the same thing back when Facebook changed the privacy policies for Whatsapp. Or when Signal changed their policies to include closed-source components. Or when Telegram changed their policies to allow ads and subscription fees. Or when Facebook messenger changed their policies to disallow 3rd party app integrations. Of course there are thousands of electronic messaging competitors to those, but just about all of them are designed to do the same thing: 1. obtain a large user base by any means possible, 2. Change things, 3. Profit off of the large user base that’s locked into using the product.
Never trust a service that cannot be self-hosted.
We lowly slave-like users are starting to recognize that pattern and are moving to things that we can control ourselves and don’t require trusting a company dictator (we can trust ourselves instead). Basically, the only messaging protocols that are not designed to screw us over are IRC, XMPP, Matrix, Briar, Bitmessage, Jami, Echo, and Email. Only one of those is mainstream and built into every internet connected phone/laptop/tablet released in the past 20 years… AND it boasts being used by the entire 5 billion user base of the internet… it’s Email. So, it makes a lot of sense to use that pre-existing, open, mature, robust, decentralized messaging infrastructure to build upon. We just have to bump up the security a bit, enable encryption, and throw on a modern chat style user interface like I suggested in my 2017 article: Why are we still using instant messaging apps at all? (archive.org)
There are numerous ways to do this and more have appeared since that 2017 article. Email is a completely open protocol & ecosystem, so there are thousands of servers, client programs, and services that you can choose from and many people are working on many different features that can be added. That diversity is a huge advantage. We’re going to make something for use with Delta Chat, because that’s an open-source email client that has the same user interface as older versions of the Signal app.
Delta Chat can be used with just about any email account and server too, so we don’t HAVE to make our own, but if you want to have much more independence, freedom, control, and privacy, you can. That’s what we’re going to do below! Just so you know, there are lots of ways to do this (mailcow, Mail-in-a-Box, hMailServer, etc. ), but our method is intended to be the least expensive while also being relatively easy. There are other methods that will be much easier, but those will require more expensive servers.
How easy is this?
Well, okay… “easy” is a relative term. If you think it’s easy to download an app on your phone, enter your phone number, credit card info, address, etc., then no… it’s going to be a lot more difficult than that. On the other hand, this is going to be a lot easier than setting up a Rich Communications System (RCS) server that works with Google Messages because you’ll probably also have to set up a wireless phone company like T-Mobile, AT&T, or Verizon to do that. It’s also a lot easier than making your own Signal app server that works with other Signal users because that’s not allowed. It’s also a lot easier than making your own self-hosted messaging server that works with WhatsApp, Telegram, Facebook, Instagram, Discord, Slack, MS Teams, Skype, etc. because that’s not allowed. So in other words, making your own Delta Chat messaging server is not super easy, but it is actually possible and that’s a lot better than the alternatives. If you are pretty good at following directions, you could actually have one up and running in about an hour.
Buy a domain
If you don’t already own at least one domain name on the internet, first of all, what are you even doing? Haha! Getting a domain is pretty easy and cheap. The prices for registration are usually yearly, and they’re usually less than $20 (sometimes free). You have to find one that isn’t already owned by someone else though. Here are a few good spots to buy a domain:
- Freenom – A Name for Everyone (some might be free)
- Register cheap domain names from $0.99 – Namecheap
- porkbun.com | An oddly satisfying experience.
- Search for the best price on domains through different registrars using: Compare Prices of All Top-Level Domains | TLD-List
- If you want to research other registrars and perhaps find one in your country, here is the full list of authorized registrar companies.
Most of those will come with domain name system (DNS) server configuration controls as well and you’ll need to use those in order to point outside traffic to your email server. You’ll have options to point your domain to different DNS servers or you can use the registrar’s DNS servers and create “DNS records” to point traffic to your servers. I would say it’s often easier to use the registrar’s DNS servers to make DNS records, so make sure you know how to do that by reading your registrar’s documentation. I’m going to use NameCheap, so if you choose that one too, here is the info you’ll need: DNS Records Explained – Types of DNS Records (namecheap.com). However, NameCheap doesn’t yet support TLSA records in DNS. If you want the upmost security in federated messaging, you’re going to want that for DANE and we’ll talk about that more later.
Get a server
Next, you’ll need a server of course. You can rent one from a cloud service, or you can build one in your office or home. If you’re thinking about putting one in your home, be warned that most consumer internet service providers don’t want you running public servers and will block the ports needed to do so. Most spam blocking systems block those IP addresses, too. Business class internet service plans are much more likely to allow you to run a server, and those are the plans that will allow you to have a static IP address as well, which is another requirement for an email server. So if you really want to build a server in your home, you may need to upgrade to a business class internet service that gives you a static IP.
Also think about how much RAM you’ll need. With this set up below, we tried to be very efficient and cost effective so each device connected to the server will take up about 14Mb of RAM and the idle server will take up about 215Mb of RAM. So if you want thousands of users, you may want to buy more server resources.
Paying a fee to rent something in a cloud service might be easier since you don’t have to go about buying hardware and putting it all together. Having a static IP address is the important thing.
I’m going to use the cheapest KVM VPS I can get from RackNerd. The normal price is $23/year, but on Black Friday in November there was a special to get one for $10.28/year. Those kind of sale prices show up occasionally for other holidays as well. I’m also going to use an Oracle Cloud “always free” virtual private server to see how that works. Below are some other virtual private server cloud services to look at. In terms of features and storage, we’re going for the smallest amount of server resources possible, so that you can choose the most cost-effective server, but you’ll definitely want a static IPv4 address and, if possible, an IPv6 address too for future proofing.
- RackNerd (Starting at $23/year, sales sometimes available for $10/year)
- Netcup (Starting at 5.26 Euro/month)
- Frantech (Starting at $3.50/month)
- SSD Nodes | VPS Cloud Server Pricing (Starting at $35/year)
- Rimu Hosting (Starting at 6.5 Euro/month)
- VPSBG.eu (20 Euro/month)
- Cloud VPS Hosting at Hawk Host (Starting at $5/month)
- OVHcloud (Starting at $7/month)
- TurnKey Internet (Starting at $7/month)
- KnownHost (Starting at $5/month)
- Shinjiru Virtual Private Server | Offshore Bitcoin Hosting (Starting at $11.90/month)
- Hostwinds (Starting at $5/month)
- Linode (Starting at $5/month) (SMTP policy)
These are worth trying too, but opening port 25 for federation with other servers may be a pain.
- Oracle Cloud (Free to try) (SMTP policy)
- Vultr (Starting at $3.50/month)
- Amazon Web Services (Free to try, hard to predict pricing) – See more instructions on Speedkills.io.
- DigitalOcean (Starting at $4/month) (SMTP policy)
- Contabo (Starting at $5.50/month)
All of those are going to let you log into the server using SSH (Secure Shell) in a command prompt. So you’ll need to use a terminal emulator on your computer or phone to log in and configure things. On Android, you can use TermUX. With Windows you can use Windows Terminal or PowerShell or the Command Prompt (See: How to Enable and Use Windows 10’s New Built-in SSH Commands). On Mac, you can use the built in SSH client in the Terminal or Putty. On iOS, there are a variety of SSH client programs available too.
Connecting will be a command like below. You’ll get the username and IP address after you rent a virtual private server (or build your own).
ssh username@IPaddress
On RackNerd, I created a Debian 10 server. Use the provided root username and password to SSH into it. I had to run the below to get updates to install properly. (When logged in as root, I don’t need to start each command with “sudo”.)
apt-get update --allow-releaseinfo-change
Then run the below to install all the updates:
apt-get update && apt get upgrade
You may also want to increase the security of your server access by using RSA keys, changing port numbers, etc. See: How to secure SSH best practices Using GPG key pairs files to log into SSH and disabling password-based log-ins will keep other people from being able to log into your server if they guess the password, but only those computers where you copy the key files to will be able to log into the server. So don’t lose that key file! Here’s some info about How to add new SSH key to a cloud server – servers.com.
If you’re using the free tier of Oracle Cloud, password based SSH log-in won’t be allowed by default, so you’ll have to download the keys that it gives you when creating a server and use those to connect. See: Log In to a VM Using SSH (oracle.com) Optionally, you can create your own keys and upload them to the Oracle Cloud virtual machine when creating the instance.
Open ports needed
For me, the ports needed by the below server software programs were already open on the virtual private server I rented from RackNerd, but if you choose a different provider, you may have to use their admin control panel or open a support ticket in order to have them open the proper ports. Those port numbers are going to be: 80, 443, 993, 465, 25, and 587. The first two are for the web server used for renewing security certificates while the others are for mail transport. Port 25 is important for transferring messages between different servers. So if you want to send messages to Gmail users or any other server besides your own, you’ll need that opened. Ports 465 and 587 are used for sending messages from your device to your server, and port 993 is for downloading messages from your server to your device.
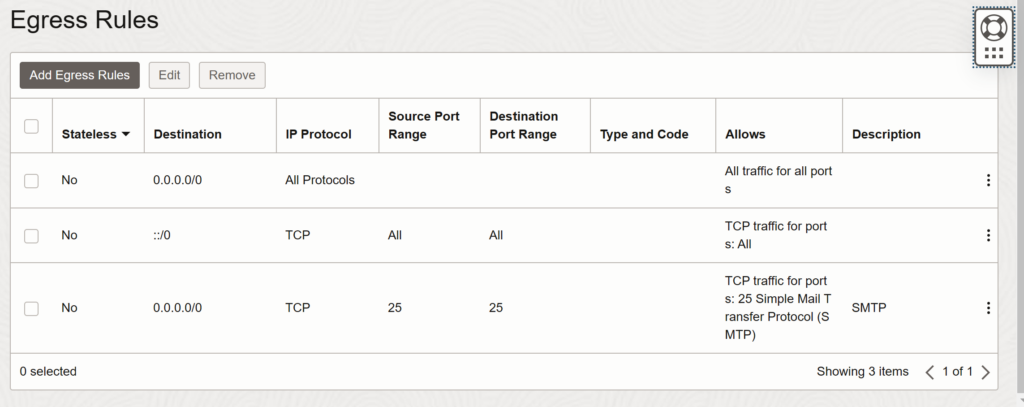
On Oracle Cloud’s free tier, you’ll need to create “ingress rules” in order to allow traffic to reach your server on those ports. See: Add an Ingress Rule to Allow ssh Access to SOA Servers (oracle.com) The Oracle Cloud Free tier doesn’t allow egress on port 25 so this may not work with external email servers, unless you switch to a “pay as you go” account, open a “Request Limit Increase” support ticket in the “Other” category, and request that they allow port 25 egress rules to work. See: CAUTION: ORACLE CLOUD >> Outbound SMTP PORT 25 is blocked – Hopping If you only want to use this with users connected to your server (no sending to external email addresses), then this will work without port 25 egress.
Also note on Oracle Cloud’s Ubuntu ARM instance, I had to use IPtables to open the proper ports to the instance server as well like so:
sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 80 -j ACCEPT && sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 443 -j ACCEPT && sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 25 -j ACCEPT && sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 993 -j ACCEPT && sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 465 -j ACCEPT && sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 587 -j ACCEPT sudo netfilter-persistent save
Test to make sure
If you want to make sure your network is capable of sending messages over SMTP, you can:
- Install a Telnet Client.
- Use this command to see if you can connect to the portquiz.net server like so:
telnet portquiz.net 25
If Telnet is able to connect (it says something like “Connected to”), you should be all set. Typing “Quit” should get you out of Telnet. For more info, see: How to manually test if an SMTP server can receive email (mailenable.com)
Check your blocklist status
Before you go further, you might want to see how many block lists your IP address is on. In most cases you can remove your IP address from the blocklist, but you might as well check first. The below tool will tell you which blocklists your IP is on already and has links to information about how to remove it.
- Email Blacklist Check – IP Blacklist Check – See if your server is blacklisted (mxtoolbox.com)
- MultiRBL lookup
- Proofpoint Dynamic Reputation – IP Lookup (Propietary block list that some businesses use.)
Set up preliminary DNS records
We’re going to want to point your domain to the server next. The step below is going to want to verify that your domain name is pointing to your server in order to generate Secure Sockets Layer (SSL) certificates on Let’s Encrypt in order to enable transport encryption.
Login to the control panel for the domain registrar of the domain you bought. Look for the “Advanced DNS” or “DNS Records” section. Some default records might already be there. You can delete those or edit them.
You’ll want:
- “A” record pointing at the IPv4 address of your server
- “AAAA” record pointing at the IPv6 address of your server (if you have one)
- “CNAME” record pointing mail.domain.com to the IPv4 address of your server
- “MX” record pointing to the mail.domain.com hostname. This is the mail exchange record that tells other email servers where your email server is.
Run the Email Wizard script
There are lots of ways to make an email server for use with Delta Chat or any other email messaging client, but I want to use a cheap server so I also want the software to be very lightweight for low memory and processor usage. If you want something that’s easier to manage or has lots more features like SQL database storage, webmail, contact/calendar sync, etc. you’ll want to look at other options, but none of that is necessary for Delta Chat. This method is just messaging and only using about 215Mb of RAM on the server.
Luke Smith has created a script that makes all of the open source software installations and configurations much easier than if you were to learn how to do it manually.
While you’re connected to your server via SSH as the root user run the below command to download the EmailWiz script:
curl -LO lukesmith.xyz/emailwiz.sh
Then change the permissions on that script using this command:
chmod +x emailwiz.sh
Then run the script using this command:
./emailwiz.sh
This will start the email server install wizard:
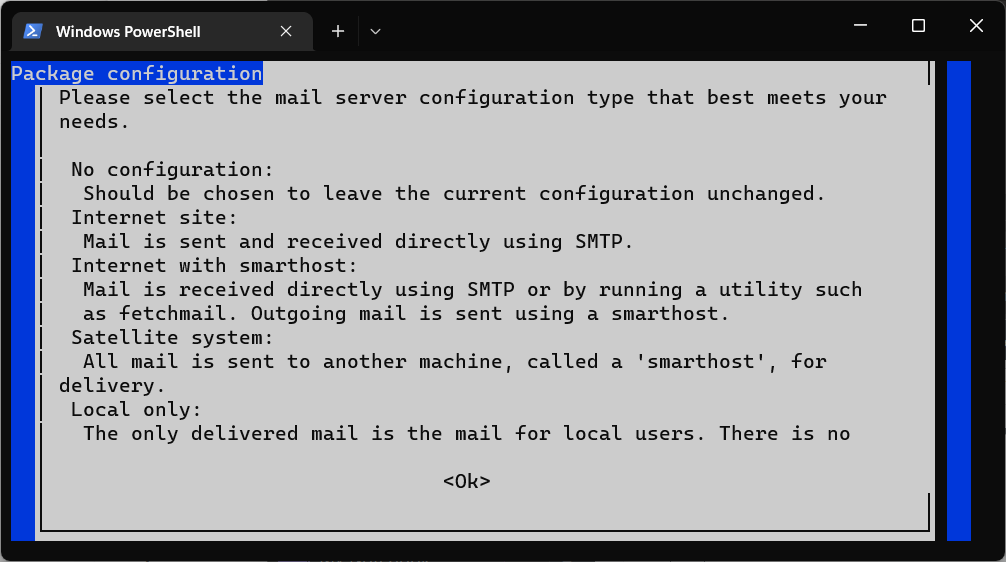
The script will walk you through the mail server set up.
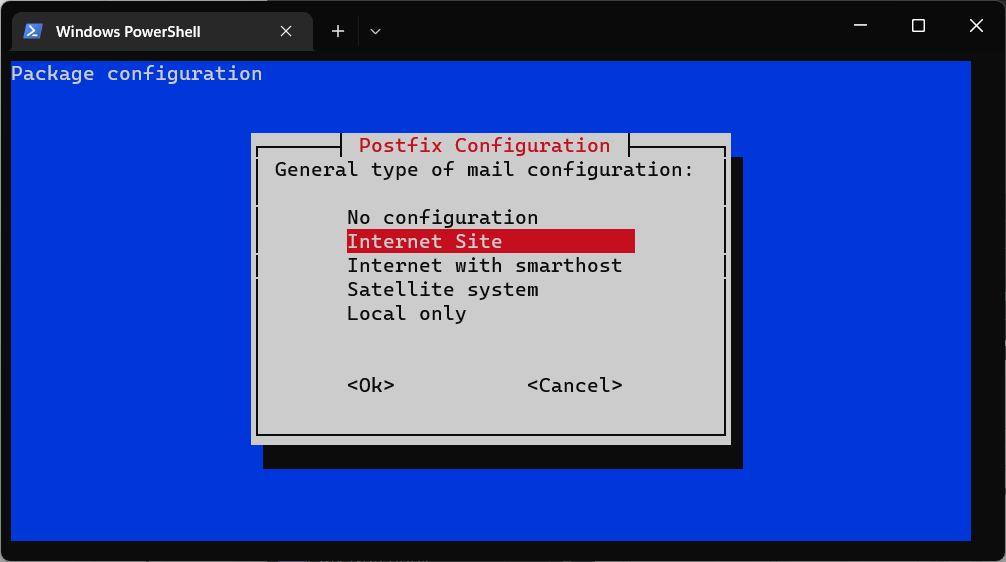
We’re going to set it up as an “internet site” so that email can be exchanged with everyone on the internet and we only need to use this one server.
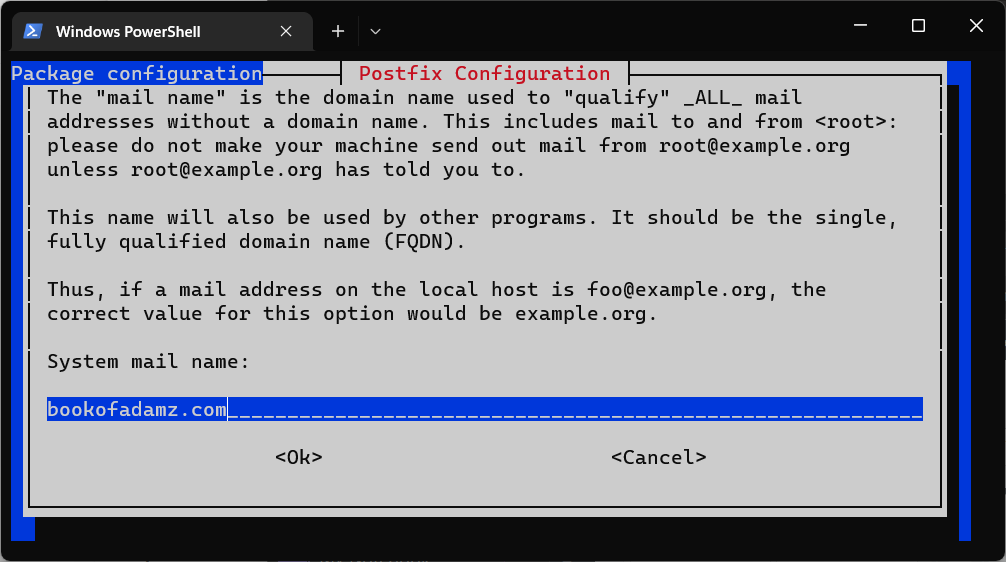
The script will ask you for your domain name and then use that to fill in most of the other configuration options.
When the script finishes, it will show you a few more DNS records to add to your DNS server. You’ll have an SPF record, DKIM record, and DMARC record to copy/paste into your DNS server’s DNS records settings. These three records are used by spam blocking systems to help verify that you’re a legitimate email server.
So back in the NameCheap advanced DNS editor, you’ll want to add a new TXT record and copy/paste the values for the SPF record that the script outputs for you. Then repeat those steps for creating new DKIM and DMARC records.
It’s becoming more important these days that you get the DKIM record correct, so here are some tools you can use to check validity:
- DKIM Checker and Lookup Tool tools | EasyDMARC – Checks for DKIM selectors in the DNS records
- Free DKIM Record Checker – Check DKIM Record – DKIM Lookup – DMARCLY – Checks DKIM status
- DKIM Check- DomainKeys Identified Mail (DKIM) Record Lookup – MxToolBox – Checks public key status
Add accounts & passwords
Next you need to make some email accounts. Since the script did all the configuration pretty nicely, it’s easy to make new accounts with the command line via SSH.
useradd -m -G mail stephanie passwd stephanie
The first line above creates the user email address “stephanie@domain.com” in the “mail” group, while the second line allows you to create a password for that user. Repeat the above commands for each person you want to be able to log into your server. Run the “passswd” command again whenever you want to change the password for someone. This server build does not have the ability to let users change their own password, so people will have to trust you as the administrator to create secure passwords and not use them to impersonate others. Or you’ll have to build something else.
Try it out!
Now log into Delta Chat and test it out: Get Delta Chat – Delta Chat. Use the “stephanie@domain.com” style email address and password that you created in the previous step and it should work pretty quickly.
The fully open-source Delta Chat app is available on Android, iOS, MacOS, Windows, and Linux. We’re using Delta Chat here because it’s a very chat-like client that also has some excellent auto-crypt encryption features and modern chat features like video/voice messages, read receipts, etc., but your new email server will actually work with any email program you feel like using.

Delta Chat should set up everything automatically simply by logging in with the email address and password you created on the server as long as the server’s hostname is something common like “mail.domain.com”.
The app may ask for permission to read your contacts, but this is only so that it can offer a contact list of email addresses for you to select and send messages to. You don’t have to allow that. You can simply type the email addresses of the people you want to send messages to. Delta Chat is open source though, so anyone can audit the code and verify that it does what it claims and does not send any of your contacts’ info to other servers.
Delta Chat supports most of the modern chat app features such as read receipts, chat bubbles, animated GIFs (via your software keyboard), image sharing, voice messages, video messages, disappearing messages, etc. The location sharing features is very cool if you want your friends to know where you are on a map. If you already have PGP keys for encryption in a different email program, those can be imported into Delta Chat and there is a procedure for transferring your keys to multiple Delta Chat app installations. You may want to turn on the “delete messages from server” option in order to keep the server’s disk space from filling up. This is also good for security since the messages will no longer even exist on the server in case that gets compromised.
A couple missing features are that Delta Chat does not show typing indicators and real-time video calling requires a little more set up in the app’s settings.
Video call server
While email is great for sending electronic text, images, attachments, etc., it really can’t do full duplex audio/video communications, but that’s ok because Delta Chat has the ability to use a separate video call server for those functions. All you have to do is specify the video conferencing server you want to use in the settings.
The main free Jitsi Meet server is https://meet.jit.si and anyone can use that if they want. It’s even suggested in the Delta Chat settings, but you still do have to type it in the field in order to enable video conference calling.
There are over a hundred other Jitsi Meet servers out there in the public. You can find a list of other Jitsi Meet servers on GitHub.
Or, if you want to continue your journey to self agency, you can make your own Jitsi video calling server, but this will probably require renting another virtual private server for an addition cost. There are lots of tutorials available about how to make your own video conferencing server using Jitsi Meet open-source software:
- How to Install Jitsi Meet on Debian and Ubuntu (tecmint.com)
- How To Install Jitsi Meet on Debian 10 | DigitalOcean
- How To Install Jitsi Meet on Debian 10 – Stack Over Cloud
- How To Install Jitsi Meet Video Conferencing Solution on Debian 10 (howtoforge.com)
If you only want to use this with a bunch of friends or family or coworkers who are all connected to the same server that you just set up, then you can be pretty much done right now. Getting the server to properly federate/connect to other external servers will take a little more work.
I would suggest proceeding to the next steps for enabling federation with other servers only if you’re planning on keeping the email server you just set up. For example, are you happy with the domain name that you used or do you want to buy a different one and start over?
Remove your IP from spam blockers
Your IP address is probably already on some spam blocking lists as those lists tend to block whole ranges of IP addresses that are not already email servers. So you’ll want to tell them that you are now an email server. It’s very easy to do in many cases.
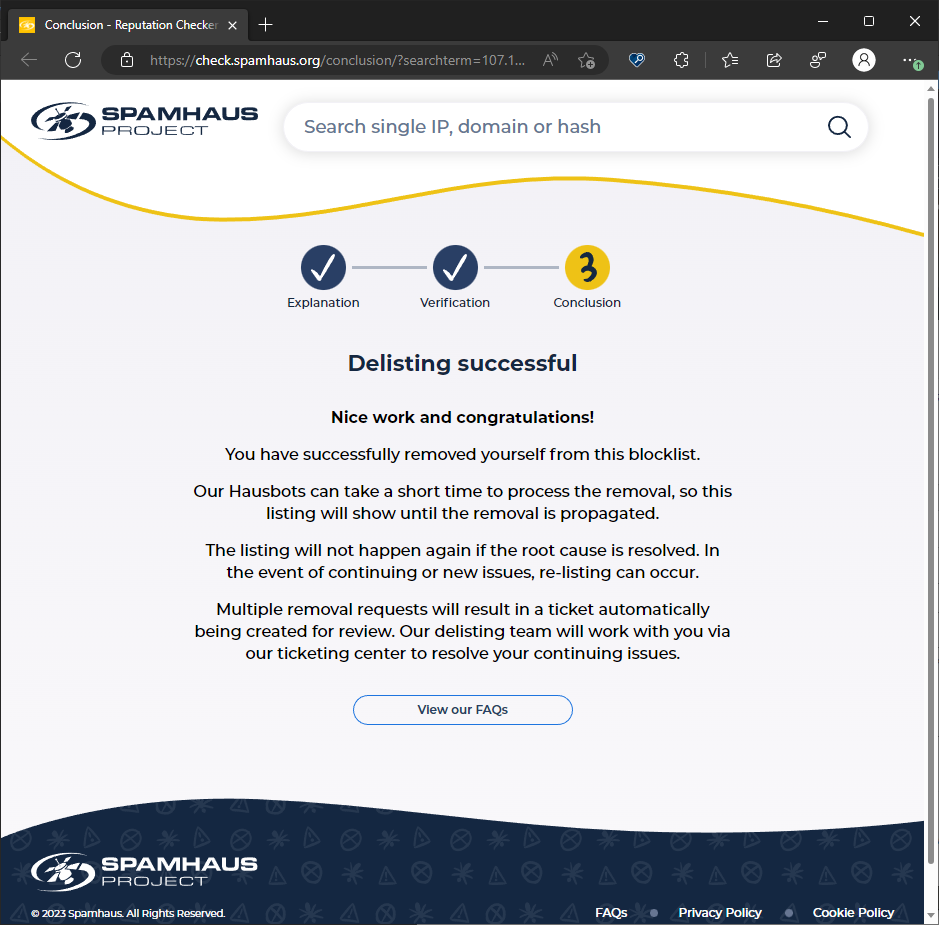
Type your mail server domain or IP address into the Blacklist lookup tool at MXToolbox. The tool will show if your IP address is on any blacklists and there will be a column for “reason”. There will also be a “details” button. If you click that you’ll get to a page with instructions about how to remove your IP address from the blacklist. I was listed on the Spamhaus blacklist and removing the listing was a matter of clicking a “I am running my own mail server” checkbox, entering an email address associated with the domain, adding some comments, and clicking “submit.”
You can also test that your server can send to everyone else using this: Email Test to check the delivery to every mail server (dnslytics.com) If you’re writing newsletters, here’s another good spam tester: Newsletters spam test by mail-tester.com Another even better email sending tester that also looks at Gmail spam, SPF, and DKIM can be found here: Spam Checker: Free Email Deliverability Test | EXPERTE.com
Then you can test for deliverability using something like: Warmy Free Email Deliverability Test: Improve Your Email Performance. Warmy can also be used to improve deliverability by “warming” the server’s IP address. Another service like that is: MailFlow.io which has a free plan. The way SMTP server “warming” works is the service will automatically send emails periodically to their own addresses that exist on other servers like Google, Hotmail, Yahoo, iCloud, etc. This way those external servers start getting used to recieving emails from your new server’s IP address and hopefully will stop sending them to the spam folder.
Register with Outlook.com
Some of the big free email servers like Hotmail/Outlook.com and Yahoo.com use their own blocklists and are a bit more difficult to get off of. You probably don’t want to be federating with Hotmail, Yahoo, and Gmail too much anyway since those aren’t super private. Hotmail/Outlook was the only big server that I had problems sending to, so here’s some tips about getting unblocked on Outlook.com. You may have to request access to Microsoft’s Smart Network Data Service using the IP address of your server. Signing up for Microsoft’s SNDS will also show you any spam complaints against your IP address generated from Outlook.com users. If SNDS says your IP address is normal, but Outlook.com/Hotmail is still blocking emails from your server, open a support ticket here. Unfortunately Microsoft seems to be block all new email servers since 2020, so you probably will have to open a support ticket. You’ll probably receive an automatic email saying that your IP is not eligible for mitigation. Reply to that email with a message explaining (and maybe showing) that you’ve done all of the “best practices” for email server security (DKIM, DMARC, SPF, DNSSEC, rDNS, etc.). You can also write about how you’re using the server only for legitimate small-amounts of communications with clients, friends, or family. A real person will probably see that message within a day and will probably unblock your IP address within another day.
Register with Google
On the Google Gmail side, you may want to register your mail server with the Google Postmaster site. This is a similar tool that will show you any spam complaints against your email server from the Gmail users’ side and will also show you your server’s reputation. If your emails sent to Gmail accounts are still getting rejected or classified as spam, you can fill out this form to let Google know.
Some spam blocking lists may want you to set up a Reverse DNS PTR record before unblocking you. See below section for more about that.
Register with Yahoo
You may also want to register your email server with the Yahoo Complaint Feedback Loop system in the Sender Hub. Look for the “Enroll Now” button on that page. This system will basically tell you when someone else reports a message sent from your server as being spam. Then you can discipline that account accordingly. The process is pretty simple, but you’ll have to be sure to create a “postmaster@<domain.com>” email address on your server to recieve the verification code at.
Set up Reverse DNS
Another important thing to enable on your server in order to reduce the likelihood of being blocked by spam blocking software on other external servers is to set up a PTR record or reverse DNS. This points your server’s IP address to your domain name. It’s basically the opposite of the A record you originally set up.
On RackNerd, I had to open a support ticket to tell them what domain I wanted the IP address to point to as they didn’t have a self-service system working at the time. This was done very quickly over email. For Oracle Cloud, the Reverse DNS setup requires a similar support request: DNS in Your Virtual Cloud Network (oracle.com)
Improve security
While your server probably works pretty nicely right now, there are some other things that you might want to do to improve security. These are going to be more advanced techniques to learn, so you may be ok with security by obscurity for a little while, but you should continue to keep up with security best practices as they evolve. Improvements are constantly being made in the open-source community.
Here are a couple good sites for testing your server to see if it’s using all of the latest security best practices:
- About the email test (internet.nl)
- //email/testTo: (checktls.com)
- Mailhardener email tools
- Hardenize: Comprehensive web site configuration test
- CryptCheck
CrowdSec
The CrowdSec security engine is an add-on that you can install and configure on your new email server to help keep aggressive hacker bots away. It may be added to the above installer script in the future, but you can install it manually if you want. Basically it’s a crowd-sourced protection system with threat intelligence and behavior analysis.
TLS Policy
Transport Layer Security is what encrypts data between servers so that we can send messages to people who are not connected directly to our specific server. In the old days, servers would connect and send data with no encryption and anyone could snoop on those messages. These days, while many servers have support for TLS encryption, some do not and by default the other servers will probably still send the message in an un-encrypted manner, and that means data leaks are possible.
Postfix has the option to require TLS by setting the parameter ‘smtp_tls_security_level = encrypt’ in main.cf, but this will keep you from communicating with servers that do not have TLS. So, a better way is to make a TLS Policy table, which is basically a list of external domains that you want to enforce encryption with. See below for more information about how to do that. It’s a bit more work as I haven’t found a publicly available list of domains that support TLS to automatically be added to the TLS policy table, but it’s good to be able to manually force encryption between specific server domains.
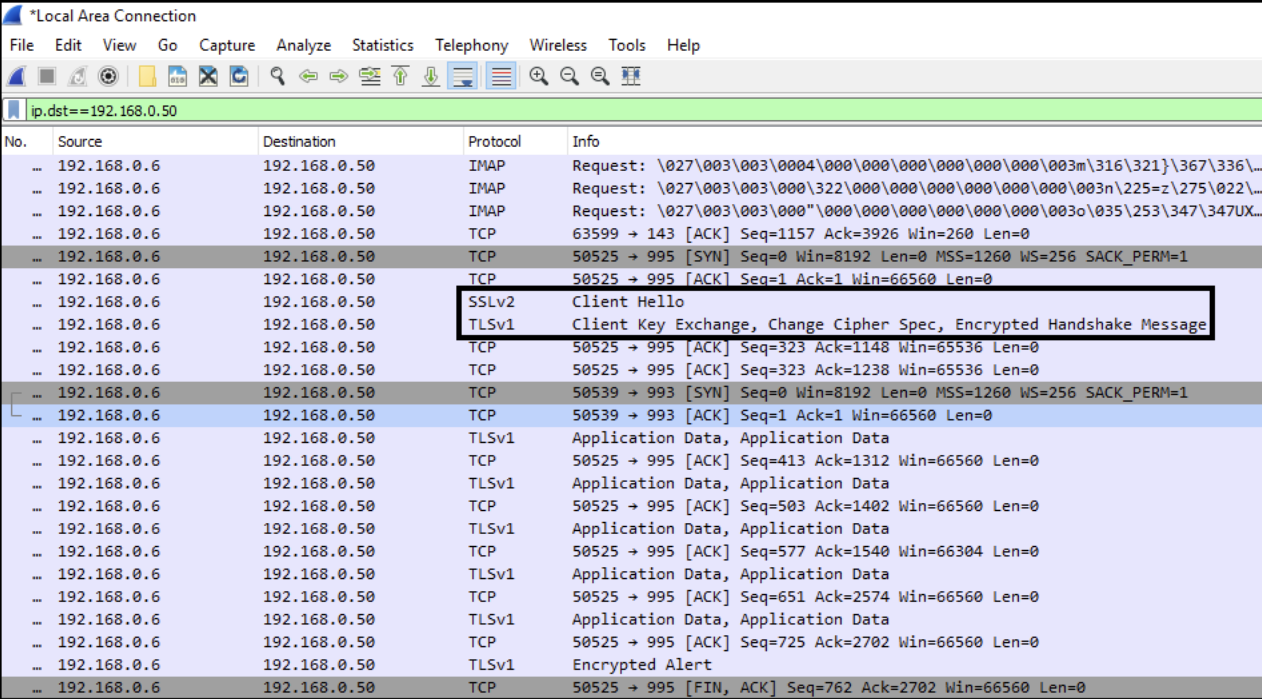
With TLS connections, no one without the private keys will be able to see the contents of the encrypted connection. Only “Encrypted Handshake Message” will be visible in Wireshark.
As other servers are upgraded, hopefully everyone will have TLS encryption by default.
DANE, DNSSEC, TLSA
TLS can still be compromised if someone spoofs the TLS certificate authority. To protect against that, we have DNSSEC, TLSA, and DANE. DNSSEC can be enabled on your DNS server and domain registrar if it is supported, then you can add a TLSA record to specify the certificate authority that your domain is authorized to use.
- DANE for SMTP how-to
- How to create a DANE TLSA record with OpenSSL – Mailhardener knowledge base
- Any chance of getting DANE with cloudflare – Website, Application, Performance / Getting Started – Cloudflare Community
- How DANE Strengthens Security for TLS, S/SMIME and Other Applications (circleid.com)
These security features are not widely available on all DNS providers just yet, so keep these future security capabilities in mind for later on when they become supported.
Encryption at Rest
We’ve got transport encryption via TLS and content encryption via Auto-Crypt, but what about at-rest encryption for everything else on the server? Of course that’s possible, too. First off, you can encrypt the entire Linux file system so that all aspects of your server will be inaccessible to anyone else who might access the hardware. There are several options for file system encryption. Then there’s a plug-in for Dovecot for encrypting stored message data on top of that.
Add more domains
All of those instructions will give you one server with one email domain, but if you want to have more domains hosted on the same server, there are some instructions here:
Multiple domains (w/ SSL Cert & DKIM for each) · Issue #283 · LukeSmithxyz/emailwiz · GitHub
I’ve also started working on a new install script that also enables multiple domain hosting:
One thing that’s not mentioned in those original instructions for multiple domains yet is certificate renewal. Certbot doesn’t do it correctly with Postfix when there are multiple domains, so we have to run a script periodically that reloads the new certificates with postmap.
sudo nano /etc/letsencrypt/renewal-hooks/deploy/reload-postfix.sh
Create a new file in the letsencrypt renewal-hooks deploy folder called “reload-postfix.sh”. Then add the below commands to the file:
#!/bin/bash postmap -F /etc/postfix/vmail_ssl.map systemctl restart postfix && systemctl restart dovecot && systemctl restart opendkim
Exit and save the file. Then whenever the certificates get renewed, postfix, dovecot, and opendkim will reload them into the mail server.
Reduce Spam
The script we used already installs Spamassassin for reducing spam, but not many rules are configured by default. Here are some good tips for configuring Spamassassin:
For some extra rules to add to Spamassassin, here’s a good config file to copy and add to:
Be sure to restart everything after changing the configuration using this command:
service postfix restart; service dovecot restart; service spamassassin restart
Conclusion
I’ve been using the new server I made here for Delta Chat on Rack Nerd for a while now and it’s been pretty excellent. I made one on Oracle Cloud as well. Messages are delivered very quickly, though obviously larger file type messages such as video recordings take a little longer to transfer. Unlike WhatsApp, Signal, and Telegram which are instant cesspools of spam as soon as I log in with a phone number, this email server has had no spam whatsoever so far! That’s probably because phone numbers are often recycled and are much easier to guess than alphanumeric email addresses. If you have excessive spam on your current email account, it’s probably because you’ve shared it with a ton of shady companies that have shared it to other shady companies over the years.
This system is set up for much greater longevity as well since I can also use any other email client program I want from the past or future. Since I’m the one in control, I can decide what does or does not change and I can be sure to treat the people I allow to use my server with respect by not suddenly selling out at some point in the future like we’ve seen with all of the other proprietary messaging apps. If my server gets too expensive someday or I want to support more people than the cheap one can handle, I can replicate the whole thing on a different server. We’ve got a huge amount of freedom!
I’ve created two servers on different domains and they communicate seamlessly with each other in Delta Chat. If you make your own, it will also be able to communicate with all of the other servers out there as well (unless you get blocked). This means you can have your own little WhatsApp competitor that still works with the other 5 billion email users around the world. No need to submit to a centralized dictatorship like WhatsApp, Signal, Telegram, Facebook Messenger, or Instagram!
Yes, it was much more difficult than just putting your phone number into WhatsApp, Signal, or Telegram, but at least it is possible to actually run your own server that you can control. It’s not possible to use WhatsApp, Signal, Telegram, Facebook Messenger, Twitter, or Instagram with your own server.
Donations and Thanks
If you implement this for your company or family and appreciate all of the work from open source contributors that built all of this software, it would be nice to donate some money to them so they can afford to keep maintaining the projects or just say thanks. Here’s a list of links to the projects used:
- Donate Money – Delta Chat – Chat style client app
- Donate to Luke | Luke’s Webpage (lukesmith.xyz) – EmailWiz script
- Support EFF’s Work on Certbot | Electronic Frontier Foundation
- nginx: donation
- Dovecot | The Secure IMAP server
- The Postfix Home Page
- OpenDKIM
- Apache SpamAssassin
Other resources
- Multiple domains (w/ SSL Cert & DKIM for each) · Issue #283 · LukeSmithxyz/emailwiz · GitHub
- valere/awesome-selfhosted – awesome-selfhosted – Gitea: Git with a cup of tea (hostux.net)
- Setting up a Website and Email Server in One Sitting (Internet Landchad) – YouTube
- 7 Best Open Source Web-based Email Clients (itsfoss.com) – If you want to add a webmail interface
- mail-crypt-plugin — Dovecot documentation – Encrypt messages stored on the server
- Ethical Alternatives & Resources – ethical.net
- hMailServer – Free open source email server for Microsoft Windows
- Mail-in-a-Box (mailinabox.email)
- Rainloop | LandChad.net – Web based email interface
- How to install Mailcow and Delta chat on a VPS (bitlaunch.io)
- Email by Jan Wildeboer
- Dockerized MailServer
- MailSlurper: a lightweight open-source email server and client (medevel.com)
- 12 Best Open Source Email Servers (itsfoss.com)
- modoboa/modoboa: Mail hosting made simple (github.com)
- iRedMail – Free, Open Source Mail Server Solution
- SELF-HOSTED | Set up and run your own Mailserver with Mailcow | DNS, Security, Installation, Test – YouTube
- Run Your Own Mail Server: A Book for Independence & Privacy by Michael W Lucas — Kickstarter
- SpamAssassin rules · GitHub
- ISPmail Guide
(Original version published here: How to make your own WhatsApp, Telegram, or Signal competitor (pocketnow.com))

Hello Neat post Theres an issue together with your site in internet explorer would check this IE still is the marketplace chief and a large element of other folks will leave out your magnificent writing due to this problem
@adamnews my experience with #Contabo was really horrible, constant problems with the VPS, filesystem getting corrupt or something like that, then they start limiting traffic in the email port and I couldn't convince them to remove the limit, because they expect that if you have high email traffic you were hacked or you are doing marketing diffusion,
I really DON"T recommend Contabo, I use netcup without problems since then, which is not in your list
Remote Reply
Original Comment URL
Your Profile
Thanks for the feedback! I had seen others recommend Contabo, but never tried it myself. Adding netcup to the list of good ones to use instead!